Data breaches and leaks are just one way your account info ends up in the hands of hackers. Sometimes they steal them the good old-fashioned way by using malware. Such infostealing software is behind a recent report about a massive data collection being sold on Telegram, with 23 billion entries containing 493 million unique pairs of email addresses and website domains.
As summarized by Bleeping Computer, 284 million unique email addresses are affected overall. (If you’re confused, a single email address can have associations with multiple websites—so there can be a larger number of compromised accounts than email addresses.) Additionally, 244 unique passwords were also stolen. The discovery comes courtesy of security consultant Troy Hunt, acting on a tip from a government contact.
Infostealing malware can be more personally dangerous than the more typical breaches and leaks seen repeatedly in the news. A data breach for a specific website only impacts your other accounts if you use weak passwords (especially if they’re reused passwords). In contrast, infostealers can steal data for multiple accounts from a single person—a potentially huge headache to clean up, depending on how many (and which) credentials become compromised. Throwaway and sensitive accounts alike can be directly affected.
To see if you were caught in this particular data dump, head to Troy Hunt’s website Have I Been Pwned, which has been updated with this info. It’s a fantastic service that allows individuals to check if their email addresses have been caught up in notable major data breaches or leaks. (However, be aware not every leak or breach makes it to the database, for various reasons.)
You’ll need to follow these steps, which apply to both new and existing users of the site:
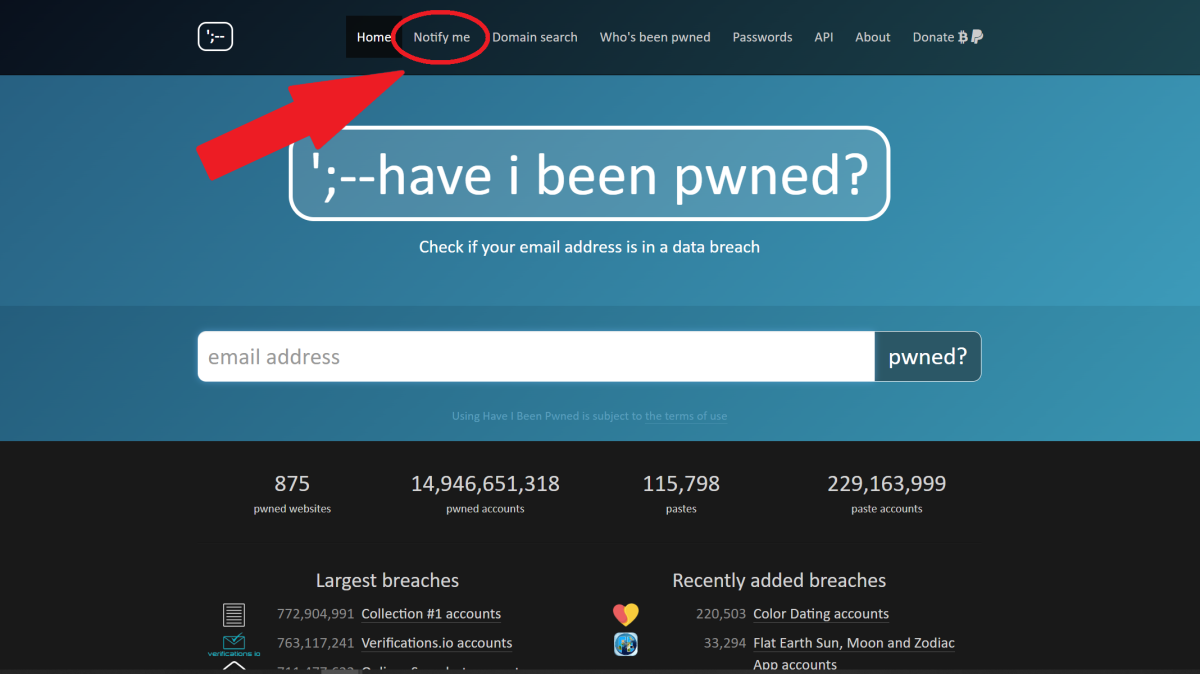
Step 1
On PC, click on Notify Me in the top menu. On mobile, tap the hamburger icon to find this option.
PCWorld
Step 2
In the popup window, enter your email address. Also complete the captcha check.

PCWorld
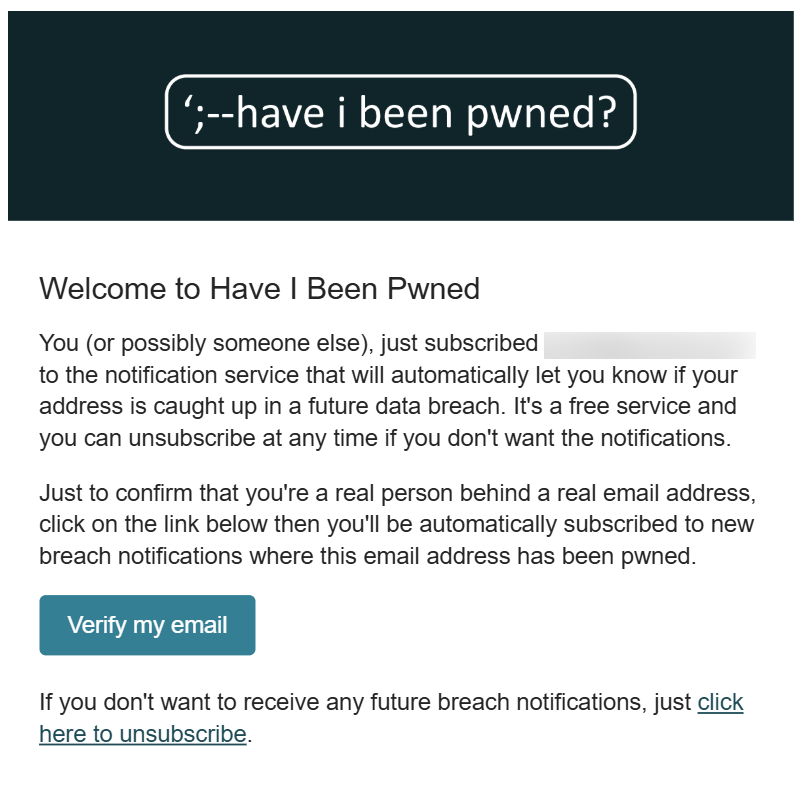
Step 3
A verification email should arrive in your inbox. If you’re a new subscriber, clicking the link will verify your address for automatic notifications of future breaches (if you’re caught up in them), and also show you a personalized set of results. If you’re already subscribed to HIBP, hit that link to see your results.
PCWorld
Step 4
Scroll to the bottom. Any data caught by an infostealer will be listed under a “Stealer Logs” section.
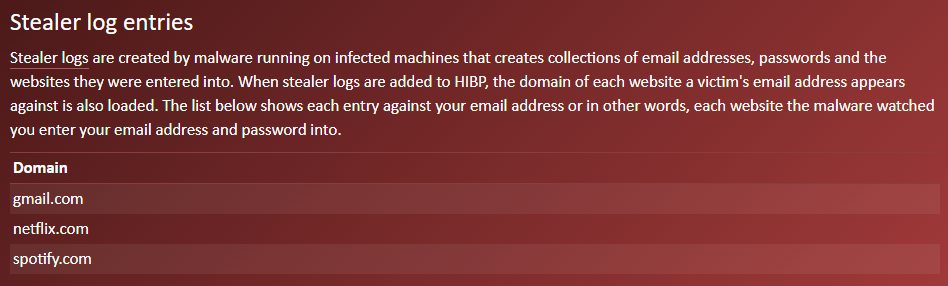
If Have I Been Pwned has records of your login credentials, as stolen by infostealing malware, this is how it will be displayed.
Troy Hunt / Have I Been Pwned
For greater security, you can only see information related to stealer logs when using this method. Performing a usual search on the website will not reveal such details.
If you’re also concerned that any of your passwords might be compromised, you can check them against a different database on the Have I Been Pwned website—Pwned Passwords. For safety, Hunt keeps email addresses and password data separate. You can only check passwords individually on the site. (For bulk checking, you must use 1Password. It’s the only password manager that HIBP has partnered with.)
Your accounts are in these stealer logs. Now what?
Before you panic—yes, your PC could have malware on it. But a couple of other possibilities exist for being in the database too. Either way, you should make sure your PC is clean of shady software including pirated apps.
(Our lists of the best free software and the best 15 open-source apps are better resources for apps that won’t infect your PC. We even have a set of suggestions for Photoshop alternatives. Just sayin’.)
What to do for your PC
- Uninstall any dubious apps you voluntarily installed.
- Double check your antivirus software is updated and set it to run regular scans. (Some malware will attempt to disable antivirus software.)
- Manually initiate a full, deep antivirus scan.
What to do for your compromised accounts
- Using the Have I Been Pwned stealer logs info as a guide, log into each compromised website and update your password. Choose a strong, random, and unique password. (Easily done with a password manager.)
- If you share your passwords with other people, be sure their PCs are clean of malware before sharing the login info again.
As for the other reasons your data might be in these stealer logs, your password may have been used by someone on a malware-infected PC. (For example, a loved one who has logged into a shared Netflix account.)
Our Favorite Antivirus Suite
Norton 360 Deluxe
Chcete-li přidat komentář, přihlaste se
Ostatní příspěvky v této skupině

It’s common sense that if you have a Windows PC, you need a third-par

As America apparently digs in for the long haul in a trade war with C


If you’ve ever found it frustrating to force-close a program in Windo

I appreciate and respect what the GDPR was trying to accomplish. The


You’ve got a Steam Deck and you’re perfectly happy with it, but you f