Psst. Do you know what apps and services are connected to your Google or Apple account?
Yes, that’s right—your online accounts may be linked to third-party apps, websites, and/or services. Think eBay, Reddit, Pinterest, and a number of other consumer sites. And not just Google or Apple accounts can have these ties, but potentially others like Facebook, Microsoft, and X/Twitter.
Further reading: Passkeys explained: How to embrace a passwordless future today
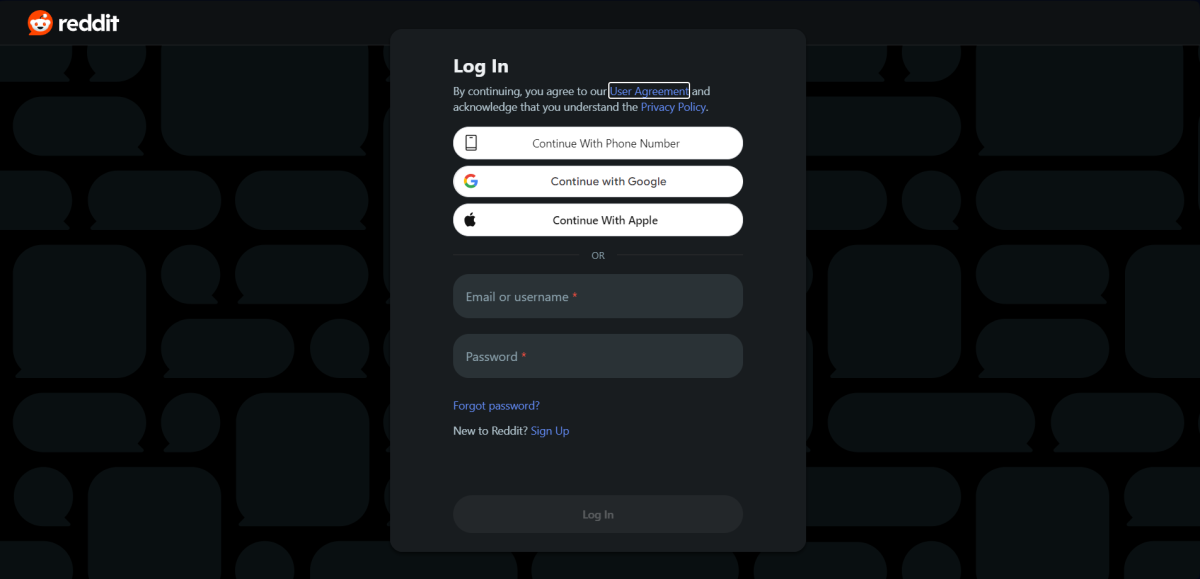
If you’ve ever logged in using the option of “Sign in with ” (e.g., “Sign in with Google”), you’ve connected an account in this way. This authentication method is a type of single sign-on (SSO), which offers users convenience and stronger security, especially compared to a weak or reused password. You don’t have to memorize anything, and it’s virtually automatic. As long as you’re logged in with your main account, you’re in. But this kind of SSO has its vulnerabilities too.
The main danger is this: If someone takes over your Google, etc, account, they instantly have access to all other linked sites. The hacker can shop in your name using any saved credit cards, dig into the details of your personal life (useful for social engineering hacks on more sensitive accounts, e.g., financial), or impersonate you more thoroughly.
(This feature of SSO enabled this business-focused vulnerability recently in the news—researchers demonstrated that bad actors could buy the domain names of shuttered start-ups, recreate email addresses for former employees, and then log into still-connected services. If any were HR platforms, sensitive information like social security numbers and tax documents could be accessed. For most people, this issue won’t affect them, unless you used a work email account to log in via SSO to personal apps and/or services—in which case, kill those connections and re-establish them with a personal account instead.)
PCWorld
Additional concerns about SSO’s other, theoretical vulnerabilities exist, too—like if the implementation is lax about session management. The upgrade of standards helped greatly reduce risks, but the potential for exploits remains.
So, if you’re using your Apple account (or other major alternative) to login to sites and want to keep doing so, you should take a couple of preventative measures:
- Secure this primary account with either a passkey (which also requires no memorization and is extremely secure), or at least a strong and unique password plus two-factor authentication.
- Look over what apps, sites, and services have authorized access. For those you no longer use, kill the link. For those you want to keep but could benefit from higher security, change your login method to a passkey, if possible.
To check to see what you might want to keep or nuke, you can use these direct links or instructions to access each major platform’s settings:
Just remember, again, if you cut off an app or service, you won’t be able to log back into that account unless you first establish an alternative method of login.
January is a good time as any for preemptive spring cleaning—digital clutter is a real phenomenon, and it’s not always harmless. And while you’re sprucing up your online security, you can also take four further steps to protect yourself—these in particular will cover your bases.
Login to add comment
Other posts in this group

Artificial intelligence (AI) has quickly transitioned from a sci-fi c

The AI goldrush is upon us, with organizations all over the world kee

Remote and hybrid work has become a major component of how many indus

Snapdragon X Series processors redefine what modern portable computin

If you’re in the market for a new gaming monitor, you don’t have to c

We regularly review the latest smart locks–deadbolts, most often–repo

When’s the last time you did some PC spring cleaning? All those unuse
