Earlier this month, an alarm sounded—security researchers at GitLab Threat Intelligence discovered a handful of Chrome extensions adding code in order to commit fraud, with at least 3.2 million users affected. But the add-ons didn’t start as malicious. Instead, they launched as legitimate software, only to be later compromised or sold to bad actors.
As summarized by Notebookcheck, these extensions provided useful features not included with Chrome like ad-blocking, dark mode, and one-click full page screenshots. In the detailed GitLab Threat Intelligence report, the add-ons became compromised through developers falling for phishing attacks or outright transferring ownership of their extension to the hackers behind this campaign. In total, 16 Chrome extensions are affected:
- Adblock for Chrome
- Adblock for You
- Adblocker for Chrome – NoAds
- Blipshot (one click full page screenshots)
- Color Changer for YouTube
- Emoji Keyboard Emojis for Chrome
- Emojis – Emoji Keyboard
- KProxy
- Mike Adblock für Chrome | Chrome-Werbeblocker
- Nimble Capture
- Page Refresh
- Super Dark Mode
- Themes for Chrome and YouTube Picture in Picture
- Video Effects for YouTube and Audio Enhancer
- WAToolkit
- Wistia Video Downloader
Google has since removed these extensions from the Chrome Web Store and since they’re malware, they should be automatically disabled as well. But they’re likely still lingering on your PC.
You can nuke them by heading to the three-dot menu in the upper right corner of Chrome, then choosing Extensions > Manage Extensions. (Alternatively, enter chrome://extensions in the address bar.) Uninstall unwanted extensions by clicking on their Remove button.
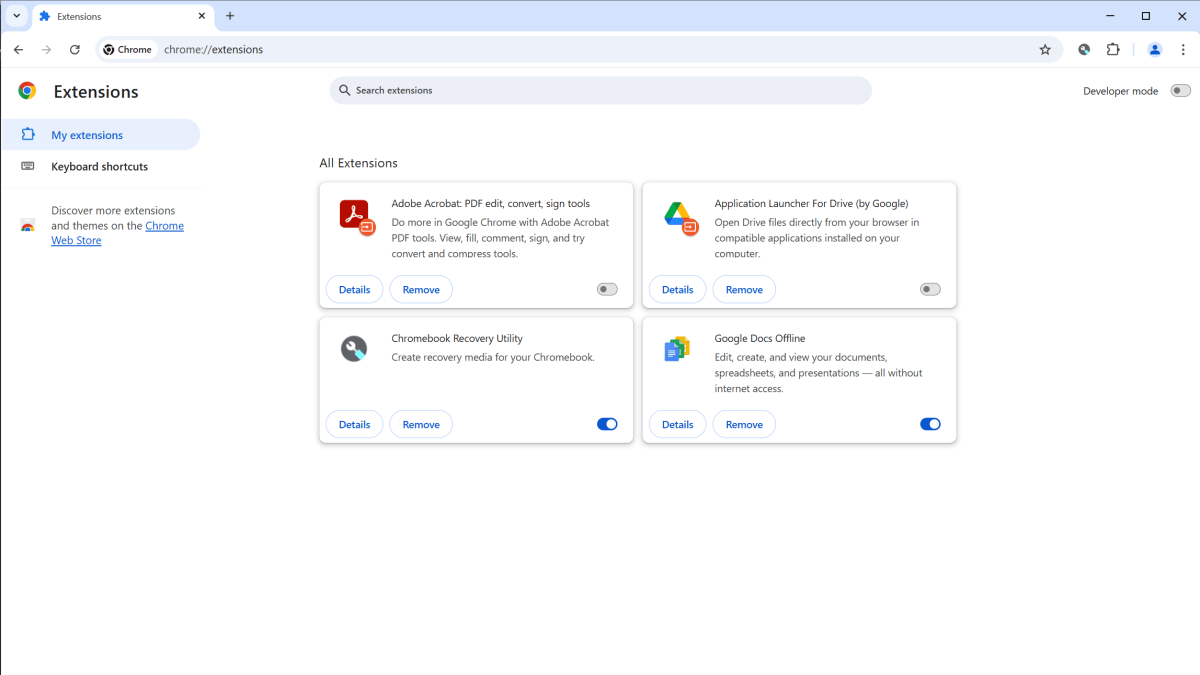
PCWorld
While you’re in this screen, you should also review other extensions on your system. Some may be flagged for violating Chrome’s policies (but not disabled) or being unpublished by their developer. Others may seem fine.
In both cases, you should take a moment to review these extensions’ permissions. The most risky is allowing the reading and changing of all data on all websites. You should only grant this permission to trusted extensions, backed by known development teams.
Speaking of, ad-blockers traditionally have always requested this level of permission, which make them better fronts for nefarious behavior. But if you’re looking for an alternative to venerable uBlock Origin (now in the process of being killed off), don’t pick one at random. A successor to uBO exists, as do other trustworthy options.
If an extension requests permissions that seem excessive to get its job done, uninstall it and use a different one instead. Also remove any that you no longer use, no need to leave yourself open to later vulnerabilities or exploits.
As for safeguarding yourself from bad Chrome extensions, be careful about what you install. The number of positive reviews and users aren’t always the full story. Also keep your antivirus software up to date. These days, a multi-pronged approach to online safety is necessary, as no one method of protection is foolproof. So yes, Google will eventually shutdown malware in extensions, but you’re safer if your antivirus catches it first or if you never have them installed in the first place.
Connectez-vous pour ajouter un commentaire
Autres messages de ce groupe


About 10 years ago, a prominent tech executive confidently informed m

TL;DR: Free shipping and 71 percent off a Lenovo 300

The Windows Task Manager is one of the most iconic tools of the opera

TL;DR: Save 36% on Microsoft Office 2024, the latest

Being a tech editor and reviewer, I’ve dealt with decades worth of de

