Most users are familiar with Windows Defender (the antivirus tool built into Windows Security), which continuously monitors the system for suspicious software activity and also identifies and blocks dangerous intruders based on a database of virus definitions.
However, no antivirus software can prevent users from installing programs that open up access to the PC like the Greek warriors with their Trojan horse.
To prevent this, it is advisable to whitelist the basic configuration of the computer. Whitelisting means that you, as administrator, create a list of all permitted programs.
Further reading: The best antivirus software
All applications that are added later are automatically blocked by Windows and prevented from running — unless, of course, you also add them to your whitelist.
In this way, you can prevent family members, school classes, or employees from secretly downloading virus-infected programs onto your PC.
At the same time, whitelisting also offers additional protection against previously unknown malware that is not covered by the virus definition lists.
A whitelist for programs
The Local Security Policy tool is included in both Windows Pro and Home. In the Home version, however, it must first be integrated via the command prompt.
Microsoft
To configure a whitelist, you need the Windows on-board tool Local Security Policy.
It is included in the Pro versions of Windows 10 and 11 as well as in the Enterprise versions. The Local Security Policy is also included in Windows 10 and 11 Home, but must first be integrated into the system.
You can read how to do this in the box “Enable Local Security Policy in Windows Home” at the end of the article.
You can use the Local Security Policy to configure the Windows Applocker feature, which has been included in all Windows versions since Windows 10 1809.
Applocker works with rules — known as policies — and is therefore comparable to the Windows firewall. You can use the function to create both a whitelist and a blacklist.
A blacklist allows all applications to run and only blocks a few explicitly named programs. However, as thousands of new malware programs with new names and files appear every day, it is more practical to configure a whitelist of existing, approved programs and block everything else.
Use the Local Security Policy tool to configure the Applocker application control, which has been available in the operating system since Windows 10 1809.
Foundry
Set up the Applocker whitelist
Type secpol in the taskbar search field and click on the hit of the same name to open Local Security Policy. Then go to Application Control Policies > AppLocker. There you will find four subfolders. The folder “Executable rules” is interesting, it deals with files with the extensions EXE and COM.
The rules can be adjusted individually for each program. However, this is time-consuming and complicated. Microsoft has therefore included an option to assign a standard rule to applications that is suitable for most purposes.
To assign a default rule, right-click on Executable rules and select “Create default rules;” and then right -click on Executable rules again and select “Automatically generate rules.”
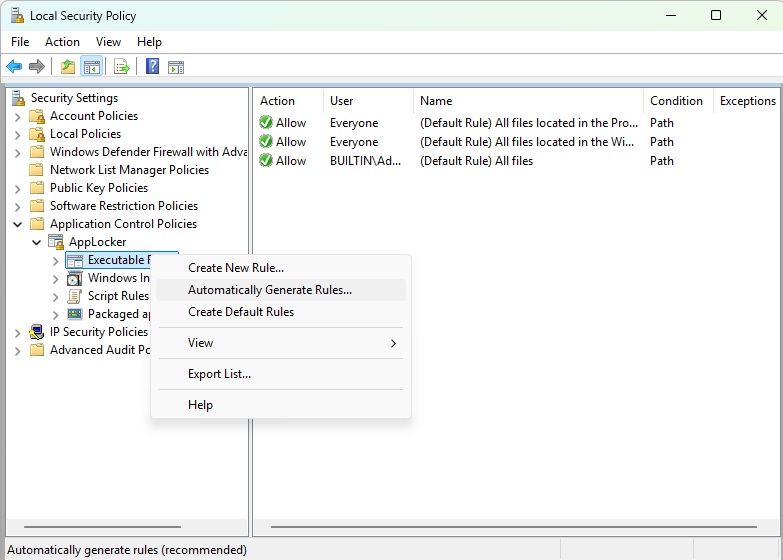
Foundry
This starts a wizard, in the first window of which the folder C:\Program Files is selected. After clicking on “Next,” you will be taken to the “Rule settings” window.
There you can choose between the options “File hash” and “Path.” This is about the way in which Applocker should identify programs: by the hash value of their EXE or COM file or by the path in which they are installed.
A file name such as Notepad.exe is not suitable for identifying an application, as many malware programs use the names of typical Windows tools to disguise themselves. Leave the default setting “File hash” and click “Next.”
Applocker now creates the rules for the applications under C:\Program Files. Click on “Create” to confirm. Then repeat the process for the C:\Program Files (x86) and C:\Windows folders.
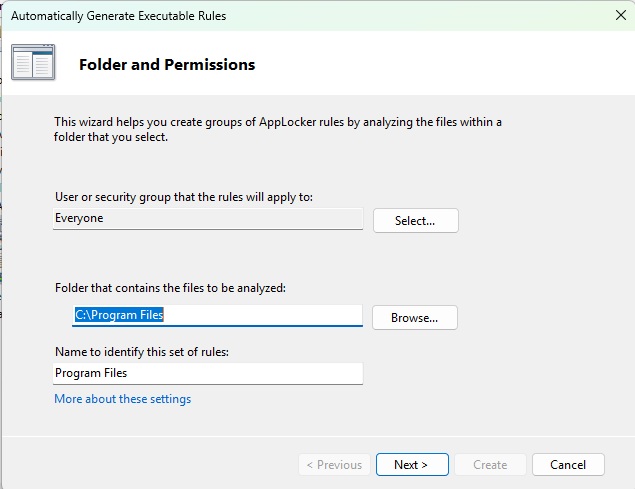
After defining the default rules, specify the folders to which these rules should be applied. The rule wizard suggests C:\Program Files or C:\Program Files as the first folder.
Foundry
Activate application identity
For Applocker to work, the Windows service Application Identity must be active.
Type services into the search field in the taskbar and click on the hit with the same name. Double-click on the “Application Identity” entry in the list and press the “Start” button.
If you now try to call up a program outside the above-mentioned folders, you will receive the error message “This app has been blocked by the system administrator.”
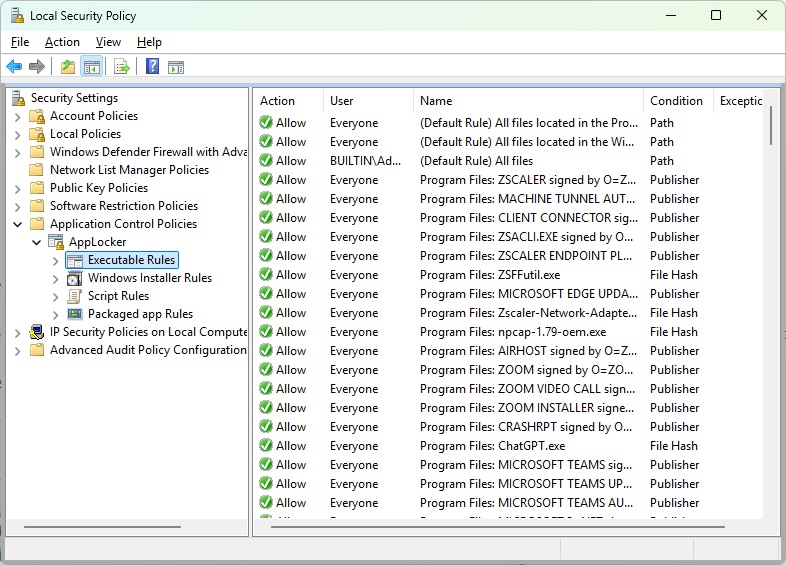
Once the configuration is complete, Applocker will display a long list of applications that are permitted to run by the whitelist.
Foundry
Only applications located in the folders C:\Program Files, C:\Program Files (x86), and C:\Windows can now be called up. Applocker has added these programs to the whitelist.
However, it is not possible for standard users to add further programs to these folders as they do not have write permissions in these folders. This is reserved for users with administrator rights.
This configuration provides you with effective protection against virus programs penetrating the system. In addition, users without administrator rights can no longer install their own software. Access to documents, image files, videos, music, etc. remains unaffected.
Try out whether you can work with Windows sealed in this way. Please note that all EXE and COM files installed under C:\Users or in other folders not included in the whitelist are blocked.
If problems occur, you only need to restart Windows. As the start type of the Application Identity service is set to “Manual,” it is deactivated after the restart. This also deactivates Applocker.
If you want to activate Applocker permanently, call up the properties of the service again, change the “Startup type” to “Automatic,” and confirm with “OK.” The service will then be loaded every time Windows is started and Applocker will be activated.
If the change of the startup type fails with the message “Access denied,” call the registry editor Regedit.exe, go to the folder
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\AppIDSvc folder and enter a “2” for the “Start” key. The change is effective immediately and can no longer be undone via the properties of the service. To return to the manual startup type, open the registry editor and enter a “3” in the above-mentioned key.
If you have accidentally locked your Windows system so that you can no longer access the registry editor, right-click on the Start button in the taskbar and open “Terminal (Administrator)” in the following menu.
You can also open the editor from the command line by entering regedit. Then — as described above — set the manual startup type again and reboot Windows.
To switch off Applocker permanently, select the executable rules in Local Group Policy, then right-click on the list and click on “Delete.”
Cyberlock as an alternative to Applocker
Applocker offers many more options than we can describe in this article. The Cyberlock tool is even more comprehensive.
It was previously distributed as freeware under the name Voodooshield and now has to be licensed under the new name for $30. You can test the program free of charge for 15 days.
After installation, Cyberlock scans the Windows installation, takes a snapshot of the applications found, and creates a whitelist.
As soon as you then download, install, or uninstall an application or start an unsigned application, the software displays a notification window in the taskbar corner.
There you must select one of the three options “Block,” “Sandbox,” or “Install”/”Allow.” You have 20 seconds to do this. If you do not respond, Cyberlock cancels the installation process.
Other whitelisting tools
Applocker’s predecessor was the Software Restriction Policies (SRP) included in Windows since XP. However, Microsoft has deactivated this function with Windows 11 22H2.
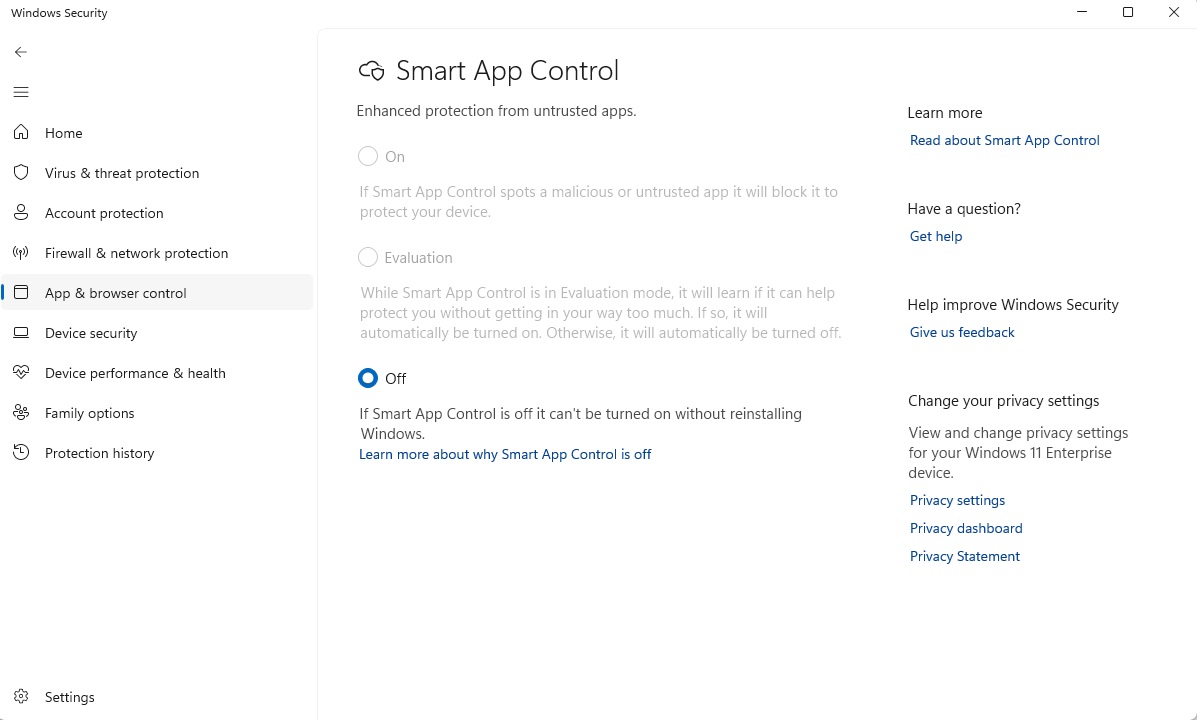
Windows Smart App Control is only activated if you primarily work with digitally signed standard applications.
Foundry
Another whitelisting tool is at best suitable for preventing Windows newcomers from installing potentially dangerous software. In the Settings of Windows, you can select the option “Microsoft Store only (recommend
Accedi per aggiungere un commento
Altri post in questo gruppo


For many of us, World Backup Day is a reminder that as protected as o

Before we know it summer will be here, but don’t wait for the hotter

If you live in a more populated area, you likely check your doors bef

TL;DR: Microsoft 365 is getting a p


I’ve been using Windows for as long as I can remember. It was on the
