Most browsers these days are pretty darn secure. But can secure browsers be optimized even further? The answer is yes! Let’s dive into some of the most important security settings you’ll find in today’s web browsers and how you need to adjust them for utmost protection.
Enable two-factor authentication
Almost all modern browsers offer the ability to synchronize data like bookmarks, browsing history, open tabs, passwords, and more. Although this is convenient, you should weigh the risks here, especially when it comes to syncing payment methods.
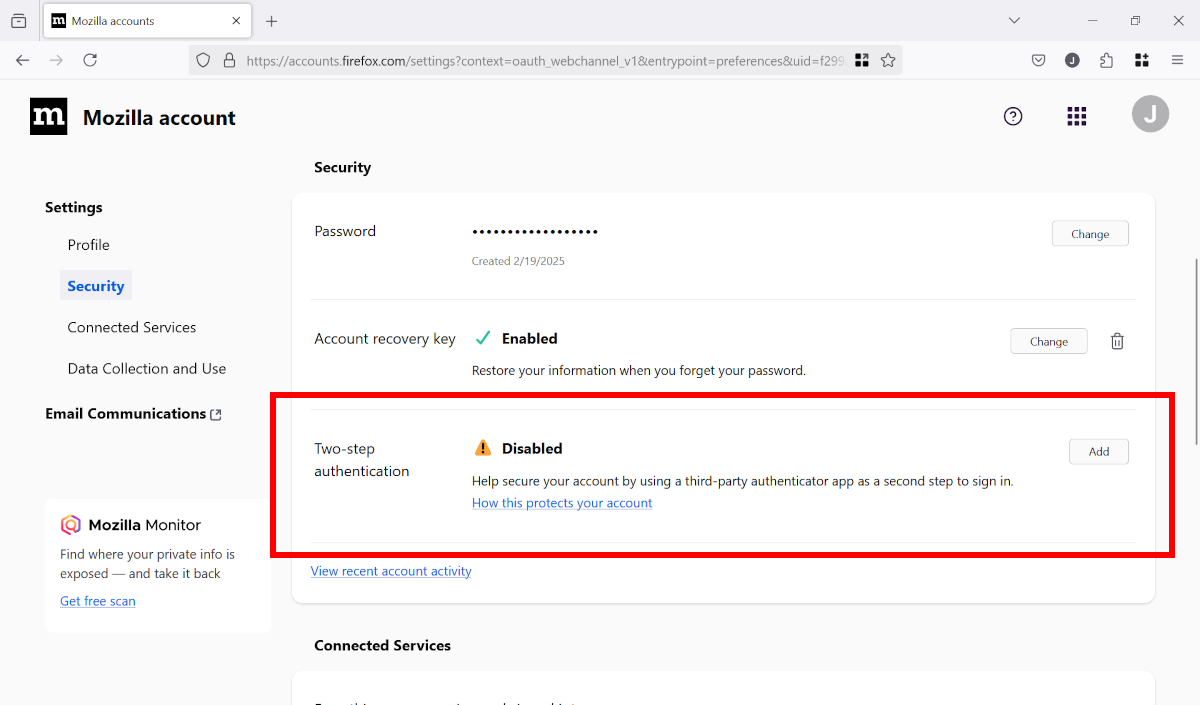
If you decide to keep synchronizing your data, make sure you secure your account with a strong password and with two-factor authentication. That means even if someone got their hands on your password, they wouldn’t be able to access your account without your phone as well.
Joel Lee / Foundry
Firefox is exemplary in this respect. To enable two-factor authentication, navigate to Settings > Sync > Manage account. Then, navigate to the Security tab and click the Add button for “Two-step authentication.” (You’ll need an authentication app like Authy or Google Authenticator.)
Disable the saving of sensitive data
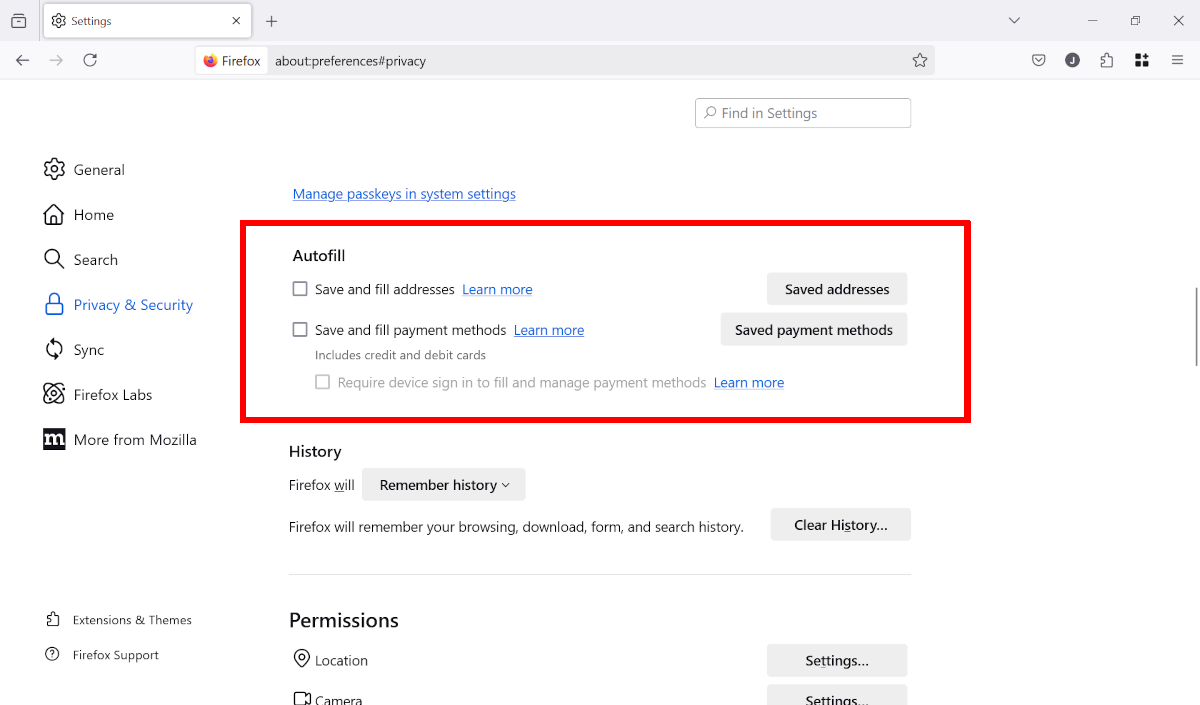
In principle, there’s nothing wrong with synchronizing open tabs between devices. However, when it comes to other private data, including credit card details, we advise skepticism. It’s better not to save such sensitive data in the first place.
Joel Lee / Foundry
In Firefox, you can do this by navigating to Settings > Privacy & Security, then scrolling down to the Autofill section. Uncheck the boxes for “Save and fill addresses” and “Save and fill payment methods.” Most other browsers let you do this, including Chrome, Opera, and Vivaldi.
Third-party cookies and other trackers
Advertisers want to be sure the money they’re investing is going to the right eyeballs, which is why third-party cookies and trackers have been so important over the last several years. They’re used to identify you and track your activity across the web, which helps advertisers target their ads to the exact demographics they want.
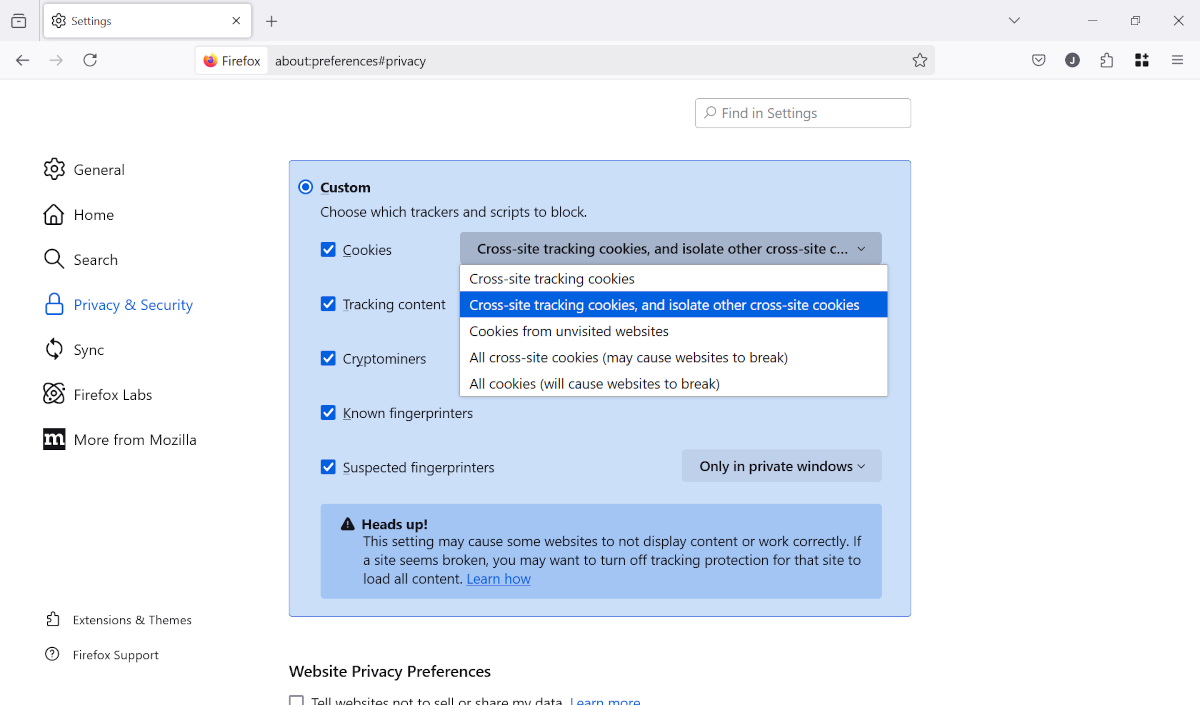
If you want to prevent this, you have to change the cookie privacy settings in your browser. In Firefox, you’ll find these options by navigating to Settings > Privacy & Security > Enhanced Tracking Protection. If you select “Standard,” you’ll get Total Cookie Protection that prevents trackers from following you between sites. For more granular control, select “Custom” and use the drop-down menus to decide what kinds of cookies and trackers you want to block.
Joel Lee / Foundry
However, cookies aren’t the only weapons in an advertiser’s arsenal. They also use something called “fingerprinting,” which combines various data points (like your browser, IP address, time zone, screen resolution, installed software, etc.) to identify who you are. If you want to protect yourself against fingerprinting, you almost have to use the Tor Browser.
Note: You might also notice a “Do not track” option in most browsers. The idea here is that your browser will tell websites and servers that you don’t want to be tracked. However, it’s up to the websites and servers to honor that request — and most don’t, so it’s functionally useless.
Encrypt your DNS requests
Whenever you visit a web page, that page’s URL needs to be resolved and translated into the IP address of whatever server is hosting that web page. That translation is done by a DNS server, and normally that request is sent to the DNS server unencrypted.
If your connection was being eavesdropped by someone, they could see which web pages you were visiting. Want your DNS requests to be private? You’ll have to enable “DNS over HTTPS,” which ensures that your DNS requests are sent over an encrypted connection. (The only caveat is that not all DNS servers support this yet.)
Joel Lee / Foundry
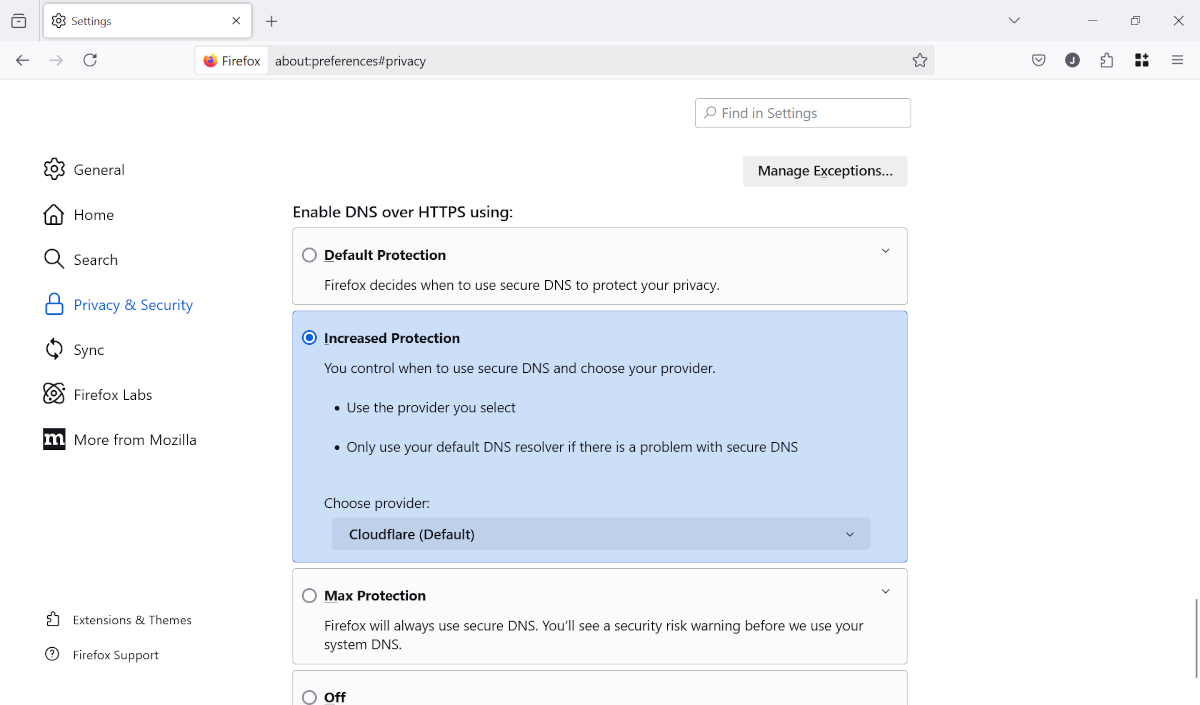
Firefox is again exemplary in this respect, as it has clearly structured language for this feature. Navigate to Settings > Privacy & Security and scroll down to the DNS over HTTPS section. It’s probably set to “Default Protection,” which is synonymous with Off.
If you switch to “Increased Protection,” you’ll select a secure DNS provider (Cloudflare by default) and Firefox will try to encrypt all DNS requests. When it fails, it will fall back to your regular non-encrypted DNS server. If you switch to “Maximum Protection,” Firefox will only use encrypted DNS requests with no fallback option.
Use bridged connections with Tor
There’s no doubt that using the Tor Browser and the Tor network is one of the most secure ways to be on the internet. With your internet traffic getting routed to different servers, the browser might be a little slower than usual, but your activity is truly anonymous.
Unfortunately, website operators and legal authorities are always trying to make anonymous web browsing more difficult. In addition, access to the Tor network often gets blocked by admins.
Joel Lee / Foundry
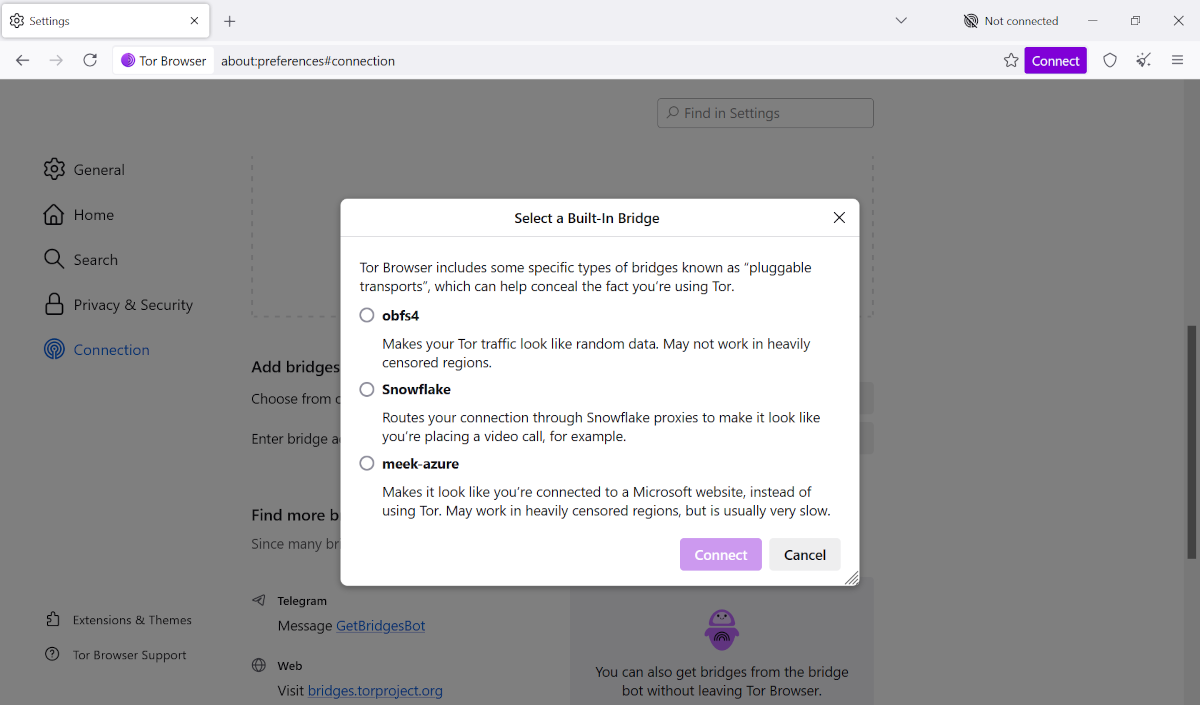
But there’s a workaround. Tor Browser offers something called “bridges,” which must first be enabled. Navigate to Settings > Connection, then scroll down to the Bridges section. Click on Select a built-in bridge and choose one, then click Connect.
There are three built-in Tor bridges: obfs4 (which makes your traffic look random but may not work in heavily censored regions), Snowflake (which routes your traffic through proxies to emulate different activities, like a video call), and meek-azure (which makes it look like you’re connected to a Microsoft website but is usually quite slow).
Further reading: What is Tor? The anonymous internet, explained
Accedi per aggiungere un commento
Altri post in questo gruppo

If you’re looking for a big, cinematic OLED upgrade for your gaming P

If you use an AI image or text generator to make a work of “art,” doe

Whether you want a security camera for keeping an eye on your home wh

If you’re looking for a big, cinematic OLED upgrade for your gaming P

Imagine a live tutor within Windows that could walk you through an ap

Microsoft Copilot is more than just a tool–it’s designed to learn you

While improving Microsoft Copilot’s basic research functions might no
