Here’s a hot computer tip coming to you straight from 1995: don’t enter random stuff in the Windows Run command bar. This might seem obvious to anyone who knows what “run” means in a PC context, but one weirdly stupid-but-ingenious bit of malware is spreading across the web this way. It’s not quite as dumb as it sounds… but it’s still pretty dumb.
The plot goeth thusly: You’re browsing a slightly sketchy site, or maybe just a normal one that isn’t as vigilant as it should be against sketchy ads. You see a CAPTCHA alert that instructs you to click the little box to show you’re not a robot. (Which is kind of a presumptuous thing for any kind of automated tool to do, but I digress.) But instead of asking you to spell out some nonsense text or click all the squares with street lights, it has a numbered list of steps for you to demonstrate your humanity.
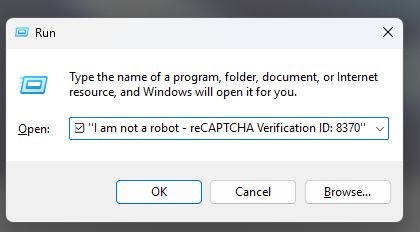
MalwareBytes Labs spotted one such CAPTCHA that demanded three unusual steps from prospective users. First, press Windows key + R. Second, press Ctrl + V. Third, press Enter.
Now, if you’ve been using Windows for even a little while, alarm bells should be going off in your head. Turns out, the pop-up “verification” is trying to get you to open the Windows Run command, paste in a bit of text that the site snuck into your clipboard via JavaScript when you clicked “I am not a robot,” and then run it. All of that is pretty sneaky, even if it only works on Windows and on less tech-savvy users.
But here’s the ingenious part: the text that the site copied to your clipboard begins as “I am not a robot – reCAPTCHA Verification ID: XXXX” or something similar. As it happens, this is exactly as much text as it takes to fill up the Run command horizontally in its default appearance. What you can’t see, hidden beyond the bounds of the Run window, is a trigger for the Mshta command that downloads a certain file from a web server.
MalwareBytes reports that these are typically disguised as media or HTML files, but in reality it’s a tool designed to hunt down personal info on your system and relay it back to a remote location, or just a good old-fashioned remote control trojan.
This setup relies on your nearly automatic response to CAPTCHA verification, a bit of ignorance for the nuts and bolts of Windows (which I think is a problem both for merely non-techy people and youngsters who are far more comfortable on smartphones and iPads than a laptop), the outdated user interface of the Run command window, and a lax security setup that allows JavaScript to run on unfamiliar websites. Like I said, it’s stupid and kind of brilliant at the same time.
Basic Windows 10 or 11 security should flag malicious files as they’re being downloaded, ditto for browser-based security that requires verification for JavaScript. But MalwareBytes researchers say they’ve seen this setup in multiple implementations with a variety of nefarious payloads, so presumably someone out there is falling for it.
Accedi per aggiungere un commento
Altri post in questo gruppo

Just having a password set on your PC in Windows 11 isn’t a sure way


TL;DR: Replace Adobe Acrobat with a lifetime license

The NHL postseason begins Saturday, April 19. Games will air on ESPN,

A mini PC can be a great, affordable alternative to a laptop if you d


Back at CES 2025, Samsung revealed their latest monitors including th