In September 2024, the Germany’s federal criminal police (BKA) and the public prosecutor’s office in Frankfurt, Germany were able to report a success: The suspected operators of the darknet platform Boystown, formerly one of the largest websites for child pornography with around 400,000 members, were identified and arrested after years of research.
The special thing about this is that the suspects were identified via the TOR network, which to this day stands for security and anonymity on the internet.
Has TOR now been cracked?
If criminals can be stopped, this is of course good news. But the TOR network is not only used by criminals.
Many press representatives and opposition members in totalitarian states also use TOR to gain access to information, disseminate news, or communicate with each other without being identified by the state authorities.
See also: What is the Darknet? How the web’s secretive, hidden underbelly works
Major international media outlets such as the BBC, the New York Times, and the NDR maintain mailboxes in the TOR network, through which they can be reached anonymously by informants. And the darknet is not all evil either. Deutsche Welle, for example, operates a website there to give the inhabitants of some heavily monitored countries free access to information.
Are all these services no longer secure? And what other options are there for remaining anonymous on the internet?
Internet connection via a proxy server
The little brother of the TOR network is the proxy server. The word proxy means a representative, and this is how you could actually describe the function of a proxy server: It surfs the internet on behalf of the user.
In technical terms, this means that you connect your PC to a proxy server, which forwards your website calls, entries, and commands to the internet and returns the responses to you. Only the IP address of the server is visible to the outside world; your own address remains hidden.
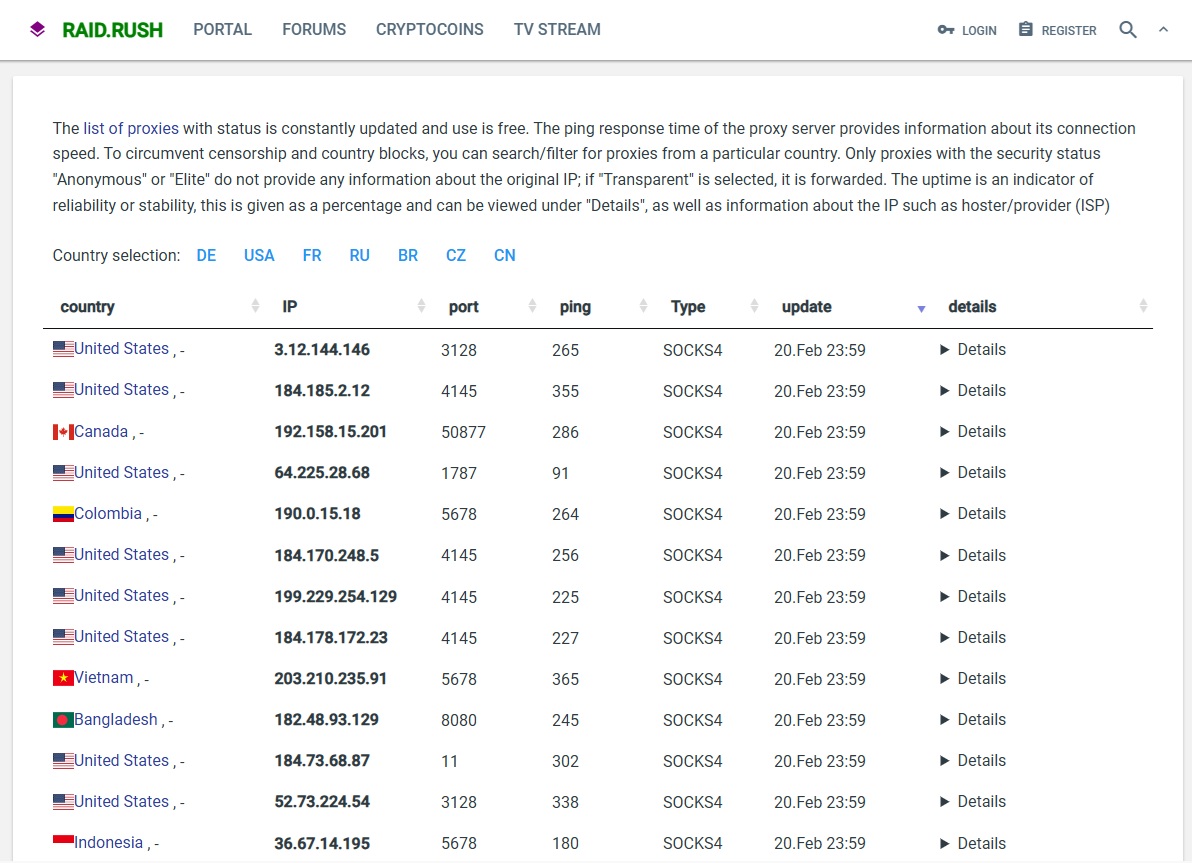
Websites such as Raid.Rush maintain constantly updated lists of free proxy servers. There are hundreds of these servers in countries all over the world, so the user can fake any location.
Foundry
You can find dozens of lists of free proxy servers on the internet, many of which also provide data on current utilization and accessibility. Examples include Raidrush and Hidemyname.
Instead of configuring the proxy server in the Windows settings (Windows icon > Settings > Network and Internet > Manual proxy setup > Setup), you can also use proxy websites such as Proxysite.com, Croxyproxy, or the free online web proxy from Steganos.
The disadvantage of free proxies is that the data transfer rates are often rather low. In addition, these services often do not offer any real anonymity, but instead name the country in which the user is based, for example, or sell the collected user data to advertising networks.
You should also be aware that many proxy servers write the data of the connections that run through them in log files, which they pass on to government agencies on request.
You can get more anonymity and higher speeds with paid proxy services. You can find a list here, for example.

IDG
VPN: Good and cheap services
If you have decided to pay for an anonymizing internet connection, you should consider a VPN service as the means. VPN stands for virtual private network.
Like proxy webites, these services also redirect your data traffic via a server on the internet, but go one step further when it comes to anonymization.
In contrast to a proxy service, the connection between your PC and the VPN server is securely encrypted, while the proxy server forwards the data unencrypted.
Further reading: The best VPN services
In addition, a proxy service works at application level, i.e. it only conceals your IP address when using the browser, for example, but not when working with an FTP client or a mail program. A VPN service, on the other hand, works at operating system level and protects all data traffic via the internet.
There is a whole range of free VPN services. However, with these providers you always have to live with restrictions, either the monthly data volume is limited, or the number of VPN servers is only in the single-digit range, or the speed is limited.
There is also a risk that these services will transmit user data to the advertising industry or government agencies.
our favorite vpn for ultimate privacy
Paid VPN services such as NordVPN, Mullvad VPN, or ExpressVPN offer high speeds and thousands of servers around the world at prices of around $3 to $5 per month.
The services advertise a no-log policy, i.e. they promise not to store any user data. This has also been confirmed in the past by independent institutions for the three services mentioned.
Blurring fingerprints
As IP addresses can change from time to time and computers from networks access the internet under a shared IP address, the advertising industry has been relying less and less on IP addresses to identify website visitors for years, and instead increasingly on fingerprinting methods.
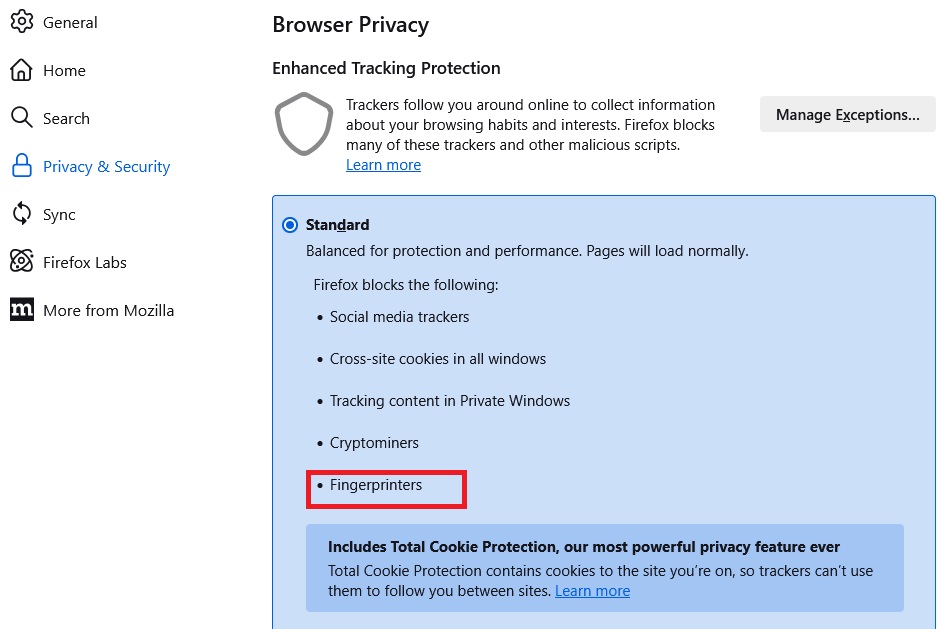
Firefox and some other browsers contain defences against fingerprinting and provide incorrect or nonsensical data in response to such requests.
Foundry
Fingerprinting does not (only) record the IP address of a website visitor, but also the configuration of their computer. Which browser is she using, which version, with which extensions, which screen resolution is set, which graphics card is installed, which driver version, which operating system …?
The browser willingly provides all this and much more data to the web server after a Javascript request. You can make fingerprinting impossible by deactivating Javascript, but this also means that many websites can no longer be used.
Firefox, Brave, and Avast browsers contain functions that either deliver incorrect data in response to Javascript requests or generally block companies that are known to use fingerprinting.
Classic tracking with cookies, etc.
When you browse the web with a browser, the websites you visit place cookies on your computer. These are small text files which, on the one hand, are a prerequisite for online shops to function at all.
On the other hand, so-called third-party cookies are used by specialized tracking companies to track visitors to a website as they move around the internet.
These companies generate a profile from the data collected in this way, which they sell to advertisers who use it to display adverts tailored to you on the websites you visit.
You can switch off the acceptance of third-party cookies in any browser. In Edge and Firefox, it is also possible to automatically delete all cookies when you close the browser, and there is a corresponding extension for Chrome called Click & Clean.
You will also find a do-not-track switch in every browser, which prevents the websites you visit from tracking you as you browse the internet. However, this is nothing more than a request. Switch the function on anyway.
Autentifică-te pentru a adăuga comentarii
Alte posturi din acest grup

The NHL postseason begins Saturday, April 19. Games will air on ESPN,

A mini PC can be a great, affordable alternative to a laptop if you d


Back at CES 2025, Samsung revealed their latest monitors including th

Secure Annex cybersecurity researcher John Tuckner has identified 57

I block every single ad on YouTube. And I’m a hypocrite for doing it.

Discord has started restricting some users from accessing sensitive c


